Our vision is to transform a programmable network into a “programmable defense infrastructure”, which supports security as naturally as it does routing. In this design, a switch not only forwards traffic, but also applies to it a wide range of defenses. The network not only routes traffic end-to-end, but also swaps defenses along the paths in and out as needed to mitigate attacks. Attacks with mixed vectors would trigger concurrent defenses, and attacks that rapidly change would be met with equally fast defense swapping. In its full force, the network would toggle a wide array of defenses rapidly on and off as traffic flows through, mitigating attacks in real time. See more details in our vision paper and the following individual projects.
Mitigating Network Covert Channels while Preserving Performance (NetWarden)
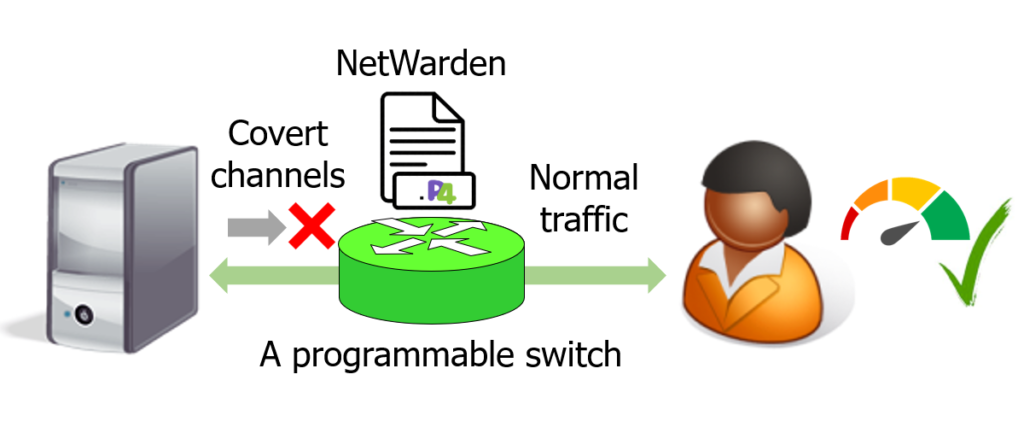
NetWarden is a novel defense platform for various covert timing and storage channels. Leveraging programmable switches, it can migrate covert channels at linespeed with little performance disturbance on TCP flows. The key design is to use a set of performance boosting techniques to temporarily increase the performance of connections that have been affected by covert channel mitigation, with the ultimate goal of neutralizing the overall performance impact. NetWarden also uses a fastpath/slowpath architecture to combine the generality of software and the efficiency of hardware for effective defense. Our evaluation shows that NetWarden works smoothly with complex applications and workloads, and that it can mitigate covert timing and storage channels with little performance disturbance. [PDF] [Github]
Ripple: A Programmable, Decentralized Link-Flooding Defense Against Adaptive Adversaries
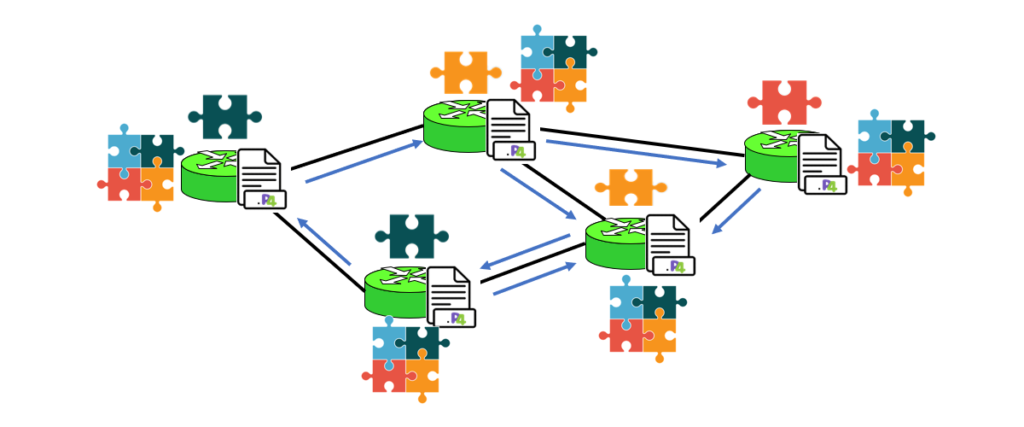
Link-flooding attacks (LFAs) aim to cut off an edge network from the Internet by congesting core network links. Such an adversary can further change the attack strategy dynamically (e.g., target links, traffic types) to evade mitigation and launch persistent attacks. Ripple is a programmable, decentralized link flooding defense against dynamic adversaries. It provides a declarative policy language for network operators to specify a range of defenses. Taking the policy as input, the Ripple compiler generates a distributed set of switch programs to extract a panoramic view of attack signals and act against them in a fully decentralized manner, enabling successive waves of defenses against fast-changing attacks. We show that Ripple has low overheads, and that it can effectively recover traffic throughput where SDN-based defenses fail. [PDF]
Bedrock: Programmable Network Support for Secure RDMA Systems
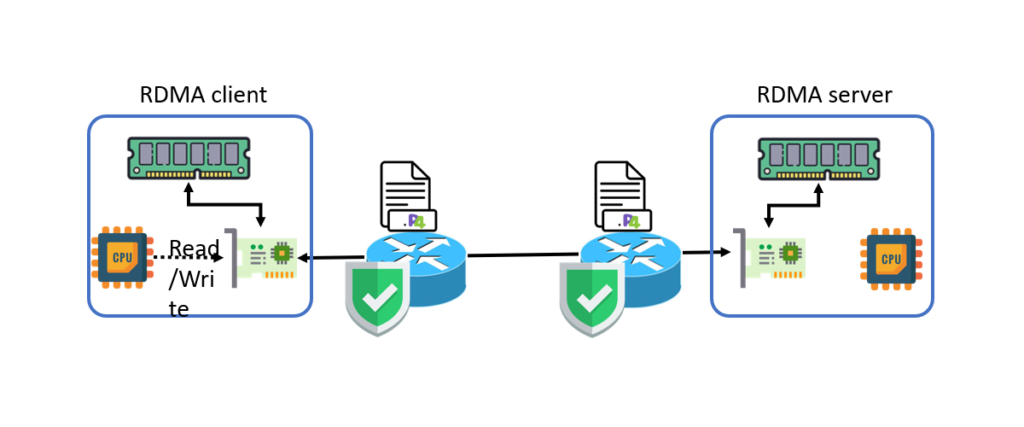
Recent findings have highlighted a host of vulnerabilities with RDMA, which give rise to attacks such as packet injection, denial of service, and side channel leakage. As the RDMA datapath bypasses CPU-based software processing, traditional defenses cannot be easily inserted without incurring performance penalty. Bedrock develops a security foundation for RDMA inside the network, leveraging programmable data planes in modern network hardware. It designs a range of defense primitives, including source authentication, access control, as well as monitoring and logging, to address RDMA-based attacks. Bedrock does not incur software overhead to the critical datapath, and delivers native RDMA performance in data transfers. Moreover, Bedrock operates transparently to legacy RDMA systems, without requiring RNIC, OS, or RDMA library changes. [PDF]
Probabilistic Profiling of Stateful Data Planes for Adversarial Testing (P4wn)
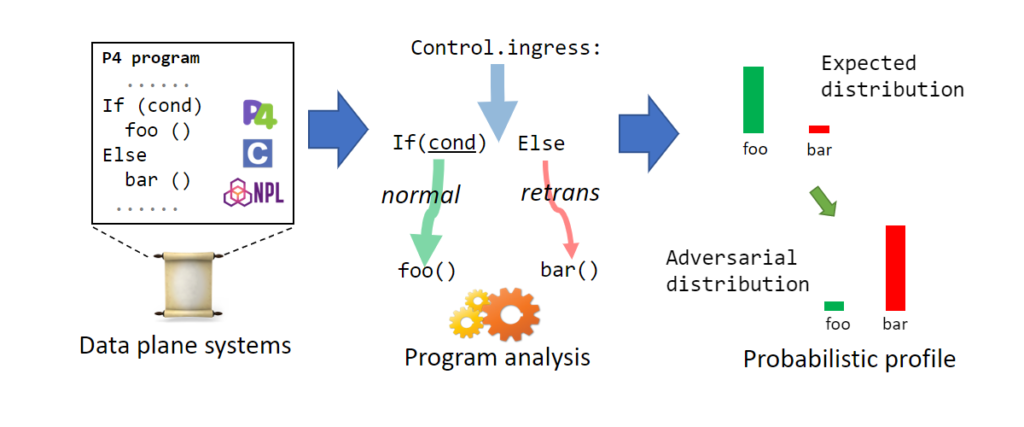
Programmable switches perform far more sophisticated processing than simply deciding a packet’s next hop (i.e., traditional forwarding). This presents challenges to existing network program profilers, which are developed primarily to handle stateless forwarding programs. We develop P4wn, a program profiler that can analyze program behaviors of stateful data plane systems; it captures the fact that these systems process packets differently based on program state, which in turn depends on the underlying stochastic traffic pattern. We showcase a concrete use case of P4wn in detail: adversarial testing. Unlike regular program testing, adversarial testing distinguishes and specifically stresses low-probability edge cases in a program. Our evaluation shows that P4wn can analyze complex programs that existing tools cannot handle, and that it can effectively identify edge-case traces. [PDF]
Secure State Migration in the Data Plane (P4Sync)
Programmable data planes enable a wide range of stateful packet processing at hardware speeds; however, protocols and systems that effectively manage data plane state remain underexplored. P4Sync is a protocol for secure state migration in programmable networks, which can serve as an important building block for state management tasks. It delivers data plane state from a source switch to a destination effectively without a software controller, while providing strong cryptographic guarantees on authenticity. P4Sync tackles several technical challenges, such as adapting memory copy techniques in VM migration, offloading per-packet security operations to the data plane, and amortizing heavyweight cryptographic overheads over a batch of packets. [PDF]
